Defining Offerings for IT Professional Services

Product marketing is a very well-defined topic, with clear advice for differentiation, go-to-market strategies, sales, branding, and the like. However, there’s a distinct lack of documented guidelines for offering professional and managed IT services. In an attempt to capitalize on the mature product marketing strategies, many businesses are working on productizing their services to solve common issues that are inherent to offering professional services.
Productization talks about creating fixed or tiered deliverables with specific timelines and prices. This is not the case with a lot of professional services, where the project itself depends on the nature of the organization, existing environment, size, regulations, business unit, budget, in-house knowledge, and other characteristics.
By nature, professional IT services are deployed on a case-by-case basis. Marketing efforts are getting prospects in the right ‘problems you’re looking to solve’ ballpark, while the details of what the service looks like are almost always on a bespoke basis.
Here is where service offerings are a very useful tool – define once, use many. Rather than going through the same motions with every prospect, a documented offering can help prospects self-serve to prequalify your service and have rich conversations earlier in the engagement.
Define Once, Use Many
An offering describes the parameters in which a service is packaged and delivered to provide enough clarity to buyers, while leaving room for tailoring the service to the customer’s environment and needs.
Development agencies, system integrators, ISVs, security consultants, and other professional services providers often subscribe to a ‘we can do anything’ approach. Within that vendor’s specialty, it could be a fair statement. By definition, a developer can develop anything. However, that’s a poor sales strategy, where prospects need to invest a lot more time and energy in initial engagements without being able to truly understand a vendor’s specialty or service capabilities.
This is a common pitfall and can be found manifesting itself in many places. For example: What’s your total addressable market? The whole world.
Most vendors’ sales and marketing collateral lack the specifics which help prospects prequalify vendors, with the level of detail staying at an ‘application development’ or ‘improve security posture’ level. Common solutions to this problem include niching down. Let’s say you would only target highly regulated industries and get all the compliance and certification in place. Or, you specialize in AWS services. Another common solution is productizing services to define off-the-shelf solutions at fixed prices with fixed deliverables.
A more suitable and strategic technique is to define offerings, which provide a way of clearly articulating what you offer to get qualified leads, have clear customer conversations and differentiate yourself, target the right customers, develop a content strategy, and build authority in the space.
In this guide, we will describe how to define an offering, best practices for writing, and we will also assess publicly available offerings from notable professional IT service providers.
Let Me Make You an Offer
Imagine being in a conversation with a prospect, and you hear one of the following statements:
- My services are latency-sensitive, so I’m looking to replatform my application to be used at the edge.
- I’m looking to deploy a proprietary machine learning technology, but I don’t have enough confidence it will behave as anticipated in production.
- I want to enable end-users to consume our services using Natural Language Processing, but the system needs to handle communications securely.
What would be your response? Generally – and this is good practice – is to diagnose the problem by asking clarifying questions. Once that’s done, we make notes of what’s needed and put a proposal together to be sent later.
Now, how would an offering look?
- To replatform applications at the edge, we have partnerships with providers that have edge compute capabilities. We select the provider following an assessment of your environment that will help us determine whether the application just needs to be lifted and shifted to operate on a VM or container at the edge, or whether it would be better rearchitected to microservices. For both options, we can use a tool such as New Relic or Datadog for observability and alerting.
- We have a framework for creating an MLOps pipeline, which also includes a human-in-the-loop system for real-world deployments that automatically shifts the decision-making process from the ML to a human when the confidence score falls below a predetermined threshold.
- Our solution for delivering services via NLP includes the integration of a large language model such as ChatGPT, and we use an API security tool such as Traceable to ensure secure communication between ChatGPT and first- or third-party APIs or databases.
What are we trying to communicate here:
- We’ve seen your problems before, and we know how to address them
- The service is already defined and available as soon as a statement of work is signed
- You have full visibility into how the service is delivered, the output, and the benefits
- Here’s our solution brief that explains everything
For all of the above, notice the level of flexibility. We are not locked in to a vendor, tool, programming language, or such. Enterprises may already have these tools in place. We are offloading their mental workload and denoting that we have the right expertise.
This is a balancing game, and the key here is understanding what enterprises need and want.
Selling to Enterprises
There’s a fantastic article by Brian Chambers, enterprise architect at Chick-fil-A, on what he and his peers look for once purchasing a tool or service. Some of the points relevant to this context include:
- We often plan really far in advance – be mindful of your clients’ financial planning and budgeting, which can be allocated as much as a year and a half in advance. Even decision-makers have their hands tied by the allocated budgets and timeframes. In this sort of scenario, an offering can help provide not only a good indicative price for an engagement, but also lowers the time and effort to scope work. Quite often, IT departments are conservative with spending throughout the year, only to realize that they have a lot of budget left in Q4 and looking for avenues to spend the remaining budget so it would be reallocated in the next fiscal year.
- We like POCs / we are slow at POCs – for professional services, a proof-of-concept is a reduced scope solution whose performance can be monitored and reported on. For example, a large website optimization project can be narrowed down to a single-page optimization project, which can be measured in terms of page load time, LCP, and the like.
- We like finding products vs having them pushed on us – reimagining this point to services, a content catalog that covers specific use cases can build authority for specific use cases. Blog posts are actually a fantastic channel to promote solutions to specific challenges or use cases. We discuss more about writing blog posts later in this guide.
Here are a few more points on selling to enterprises:
- Predictability and consistency – by having a pre-defined and documented set of deliverables, IT buyers have an easier time understanding the engagement and outcome. Enterprises can more easily conduct impact assessments, produce business cases or proofs of concept, get approvals from management and finance, and select vendors that can demonstrate they tick boxes earlier in the engagement.
- Ability to deliver on an existing strategy – business cases are produced far in advance and get multiple stakeholder sign-offs. Once these are approved and budgets are allocated, the project managers need to deliver on the details agreed upon by the wider business. With respect to the way we defined an offering (i.e. service packaged and delivered to provide enough clarity to buyers, while leaving room for tailoring the service), an offering can indicate to buyers that the services are a good match for their existing strategy, without locking in to any technology or vendor.
- Governance and reporting – must-haves for enterprise engagements include governance and reporting capabilities, which are typically delivered through dedicated account and project managers, regular progress reports, and demonstrating abilities to deliver services in compliance with HIPAA, PCI-DSS, or other standards applicable to regulated industries.
- Testing and validation – following the design and implementation of a project, enterprises have a requirement to understand the performance and reliability of the new service before it gets deployed in production. Tests that can be conducted include user acceptance testing (UAT), penetration testing, performance benchmarks, unit testing, integration testing, and system testing.
Framework for Writing a Compelling Offering
A well-defined offering covers service aspects such as definition, title formulation, description and use cases, challenges addressed, methodology, and the expected deliverables and outcomes. This framework is not categorical. It can help define the information that should be present, but the structure or flow of an offering needs to make sense depending on how the offering is documented (i.e. website copy or solution brief), and the service itself.
Service Definition
The first step in writing a compelling offering is defining what the service is. These can take one of the following forms:
- Consultancy, advisory, strategy – done with you. Output is a written artifact or a presentation.
- Professional – done for you, once. Output is a digital product, environment configuration, or service improvement.
- Managed – done for you, continuously. Output is the outsourcing of an IT function to a third-party provider.
Alternatively, the above list can also be presented as design, build, and run.
Following that, we need to define the scope of the service. As such, we need to determine the following:
- Core activity – development, design, system integration, assessment, technical support
- Output – website development, compliance audit, mobile application, enterprise resource planning configuration, security operations center, network design, security policy definition
- Target market or industry – local government, national government, eCommerce, telecommunications, multinational corporation, healthcare or financial services provider.
- Tooling or technology – public cloud, VMware, headless CMS, workflow automation, distributed databases.
- Use cases – real-time website analytics, global content delivery, auditing and compliance, cost optimization, product development,
Note: The wider the scope, the lower the resolution.
How to Write Service Definitions
In formal logic, there are eight rules for writing a definition. These are a surefire way to consistently compose them clearly and concisely. The definition must be:
- Encompassing – the definition must be both exhaustive and exclusive. This means that the definition must not be too wide – to include aspects that are not in scope; or too narrow – to exclude aspects that are in scope.
- Serverless computing allows developers to consume resources on a pay-as-you-go basis. Too narrow – there is more to serverless than just the pricing model.
- Serverless computing is a model of outsourcing infrastructure. Too wide – there are other models of outsourcing infrastructure.
- Essential – The definition must express the essential points of the term you are defining.
- Network Function Virtualization allows for easier management of networking resources. While it is true, this definition misses the point of NFV, namely that it abstracts the capabilities of a physical appliance into a virtual construct.
- Not circular – A definition must not contain the term that is being defined.
- The Internet of Things connects everyday things to the Internet.
- Replaceable – The defined term must be able to be replaced with its definition. This is a great test to see whether the definition holds up.
- Multi-factor Authentication (MFA) is a credential verification method that requires the provisioning of two or more verification mechanisms to gain access to an IT resource.
- I always need to go through MFA when I log in.
- I always need to go through the authentication method that requires the provisioning of two or more verification mechanisms to gain access to an IT resource when I log in.
- Positive – You must say what a term is rather than what it isn’t.
- Autonomous vehicles are not driven by humans.
- Industry-specific – The definition must be written in the context of the industry. For example, access controls for buildings is different from access controls for IT resources.
- Clear – The definition must not contain figures of speech, metaphors, or ambiguities.
- DevOps is every developer’s dream.
- Objective – The definition should not contain marketing speak, epithets, or hyperbolae.
- Intent-based networking is a world-leading solution that can instantaneously provision fully optimized networking configurations for break-neck speeds.
Applying the Eight Rules
For a real-world example of seeing these eight rules applied to define a new category, we will look at Andrew Green’s definition from the GigaOm Report on Edge Platforms:
Edge Platforms leverage globally distributed infrastructure to deliver content, computing, and security closer to end devices, lowering latencies, offloading networks, and improving service performance.
- Encompassing – it describes at a high level the whole Edge Platforms space, which includes content, compute, and security.
- Essential – it notes the focus on geographically distributed infrastructure
- Not circular – the words ‘edge’ or ‘platform’ are not found within the definition
- Replaceable – It can be used within a sentence to replace the term ‘edge platform’ (it wouldn’t be feasible to do so, but the point is to see if the definition holds up)
- Positive – all statements are positive
- Industry-specific – it is specific in the cloud and networking space of enterprise IT
- Clear – every term used has well-defined meanings
- Objective – the definition does not contain overinflating terms
To walk the walk, here is the definition of what an ‘offering’ is from the beginning of the book.
An offering describes the parameters in which a service is packaged and delivered, enabling prospects to pre-qualify a service, while leaving space for tailoring the service to the customer’s environment and needs.
Title Formulation
The title of the offering must be a clear representation of the service. Generally speaking, it must include at least the target and action.
|
Target (To what you do) |
Action (What you do) |
Additional identifier |
|
Cloud |
Migration |
to AWS |
|
Data Center Network |
Design |
With Cisco ACI |
|
Website performance |
Optimization |
For eCommerce |
|
Application |
Development |
using Kubernetes |
Challenges
Write challenges such that they imply your solution. The opening line is precious real estate, so packing both the pain point and solution in a single line will make sure you won’t end up with:
“In a post-Covid world, cybersecurity is of paramount importance.”
The above is a real-world example from a reputable vendor.
Let’s look at an example of an unclear opening paragraph that highlights the challenges:
- Organizations have been monitoring applications for almost as long as they built those applications. However, with the adoption of microservices and distributed systems architectures, this space has become much more complex.
Rewriting it to imply the solution, we produce the following:
- While Kubernetes makes managing a containerized infrastructure much easier by creating levels of abstractions such as pods and services, it also requires monitoring for distributed applications, the containers running them, and Kubernetes itself.
Here are some more examples of well-written challenges:
- Early approaches to cloud adoption focused on infrastructure and application migration, with very little attention to the underlying code.
-
-
- Implies an Application Modernization service (see section on Rackspace’s offering below)
-
- Federal government agencies have a higher threat profile than many of their commercial counterparts, coupled with institutional constraints in acquiring, hiring, and implementing the critical resources needed to fully protect their agency.
-
- Implies a Managed Security Service for Federal Government (see Accenture’s MSS for Federal Government below)
So how do you do that? Here is a framework you can use:
- [Something is good, or better than before] but [has these limitations that must be addressed].
- [Something is difficult] because [of specific industry or technology requirements]
- [People usually do this] but [they don’t pay attention to this]
Service Features
These are the functional aspects of an offering that describe how the end result of a service is achieved. While the service definition describes what it is and what it does, the feature provides additional capabilities that enhance the core activity of the service. To understand how to identify a service’s features, let’s look at the following two examples.
|
Data Infrastructure Migration to Cloud Architecture Move data, infrastructure, and services from on-premises or legacy systems to scalable cloud environments.
|
|
Data Architecture Optimisation Design scalable and modular data infrastructure to support data-driven business processes.
|
Highlighting the Methodology
Most professional services have a similar methodology, which takes a high-level form of:
- Discovery or assessment
- Design or planning
- Development or implementation
- Testing or validation
- Production deployment
- Monitoring and iteration
The key here is not the methodology itself, but the low-level details for how each is carried out. For example, the methodology for a web performance optimization service can say something along the lines of:
- Discovery or Assessment – We understand your environment using a pre-defined checklist of 42 line items covering relevant entities and common misconfiguration.
- Design or Planning – Upon completing the assessment, we create a high-level design draft and present it to the project’s leadership team for approval. Following the approval, we produce a low-level design and validate it with stakeholders from the business units impacted by the change.
- Development or Implementation – The changes are implemented following an Agile method. All changes are tracked in Jira as a project management software. Each deliverable provides visibility in the development process and adequate sign-off procedures.
- Testing or Validation – the solution is stress-tested in a sandbox environment and performance is monitored using a third-party tool such as Catchpoint to test between the old and new page
- Production Deployment – We implement roll-back mechanisms to revert to a previous state in the scenarios where the service does not perform as expected.
- Monitoring and Iteration – We deploy and configure observability tools such as Datadog and New Relic to track performance.
Deliverables and Outcomes
Outline the main deliverables or outcomes the client can expect from your service. The outputs can take one of the following forms:
- Written artifact – vulnerabilities assessment report, audit result, quality assurance, and user acceptance testing report.
- Digital product – website, mobile application, SaaS solution, web services, data analytics solution
- Service deployment, configuration, and optimization – high availability and disaster recovery, firewall deployment, CDN configuration, ERP configuration, zero-trust implementation, and network segmentation.
- Service improvement – application security, website performance optimization, API integrations.
- SLA-based services – technical support services, managed network operations center, managed security operations center, managed infrastructure services.
Here is an excerpt from one of Palo Alto Network’s Deployment Services for Prisma Access:
|
Palo Alto Networks offers Deployment Services for Prisma Access to ramp up your implementation and align it with best practices. Our experts will guide you through the design and deployment of Prisma Access in your environment to safely enable remote networks and mobile users in the cloud. Once the Services are conducted, you’ll have:
|
Assessing Real-World Offerings
Let’s look at three examples of Application Modernization services from notable vendors in the industry and see what they do right and what can be improved.
Note – we are not evaluating the vendors’ capabilities, but rather the way the services are communicated in these publicly available assets.
Also note – large and reputable vendors are able to get away with unclear offerings, only due to the wide reach, existing customers, word-of-mouth, and large marketing budgets.
Cognizant’s Application Modernization Offering
(Up to date as of July 2023)
The Application Modernization service is built on top of Cognizant’s Modernization Acceleration Platform to help businesses migrate to the cloud for better scalability and refactor or redevelop legacy applications to better deliver digital services.
The core idea of the offering is fairly clear. If I have a monolithic application hosted in an on-premises environment, then Cognizant’s offering can help me migrate that to the cloud following a set of best practices, where new developments and iterations are easier to deploy. However, for most audiences in the enterprise IT space, this whole concept is already implied in the name of the service – application modernization. What is missing are the specifics of what I get from Cognizant.
Strengths:
- The descriptions are on-topic, and we understand that as part of the application modernization service, we include cloud migrations and legacy application redevelopment.
- We understand that the service is carried out using one of Cognizant’s proprietary platforms, the Modernization Acceleration Platform.
Improvements
- Cognizant’s application modernization offering is diluted as it is presented in a wider context along with two other services and three other platforms. While this is not inherently a problem, there is a distinct lack of detail and the absence of additional collateral makes the offering vague. Remember, the wider the scope, the lower the resolution.
- A fairly large number of words do not provide neither information nor value. For example, ‘We help organizations deliver maximum digital value and unleash an unbeatable competitive advantage by leveraging modern software engineering principles’. Terms such as maximum digital value, or unleash unbeatable competitive advantage do not communicate anything. As a reader, I don’t have a better understanding of the offering, nor do these claims incline me to choose this service over a competitor. Similarly, modern software engineering principles are not correlated to improved performance, cost, or user experience.
- Some statements are hard to decipher. For example, ‘Application-led cloud migration’. What is application-led about the migration? Are they using applications to migrate to the cloud, or is the transfer of on-premises applications the top priority?
- The details of the Cognizant Modernization Acceleration Platform are also limited. Looking further into this, there is currently no other asset that explains what the platform is. ‘Our platform enables automated discovery, portfolio analysis and execution planning’ – this statement raises more questions than it answers. For example, what does the platform autodiscover? Does portfolio analysis mean that the platform (not IT professionals) analyzes the range of applications currently in deployment and provides some insight into how they can be improved? Does the platform suggest how the migration needs to be executed? If so, what does it suggest?
PWC’s Application and Data Modernization
(Up to date as of July 2023)
PWC’s application modernization offering is well-placed in the context of the wider portfolio and communicates fairly well the service’s features. Readers with knowledge of IT can determine from PWC’s offering if it is suitable for their business.
Strengths
The structure of the page is solid. The introduction sets the scene well for what the service is and how it fits in the wider picture. The following section splits the service into the application and data components, explaining each one individually. The ‘our approach to modernization’ describes the methodology well, quoting a number of compute models that can be used in the cloud. The benefits section also helps readers align their needs and intent with what the service can deliver.
Improvements
While the opening paragraph sets the scene well, the ‘challenges’ or ‘need’ paragraph fails to provide anything of substance.
The offering includes both application and data modernization, and while the application modernization is explained well, data modernization falls short. Just as above, the wider the scope, the lower the resolution.
The choice of words denotes that the web copy was written by a non-technical person. For example, ‘redesign new cloud architecture and operating systems’. I cannot imagine any redesigns of operating systems as part of this service. Perhaps it refers to migrating from on-premises Windows to Linux-based containers, but it definitely subtracts from the value they are trying to communicate. Similarly, what are ‘cloud service providers (CSP) funding models’? Another questionable statement includes ‘Serverless allows developers to focus on your application development instead of the headaches of managing and operating servers or runtimes’. There are plenty of situations where developers would prefer the headache of managing infrastructure instead of using serverless.
Missing – the offering talks about what PWC can do, but not what they do.
The benefits section talks about very high-level concepts of improved ROI, and breaking free from the ruthless shackles of legacy systems. However, we are missing tangible information on the expected outcome, such as a ‘lifted-and-shifted application hosted in the cloud with high-availability designs, hosted in an availability region closest to your head office.
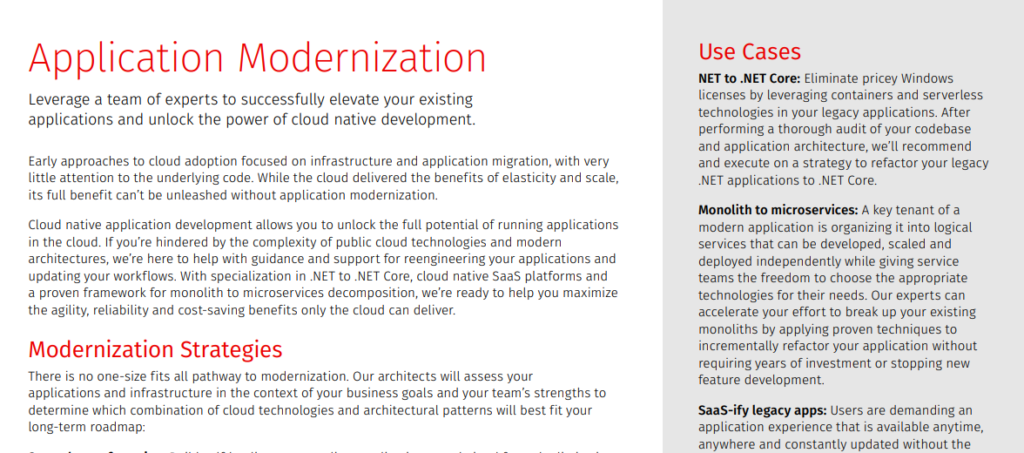
Rackspace’s Application Modernization Offering
(Up to date as of July 2023)
Rackspace have positioned themselves in an advantageous position, having published this service not as website copy, but as a .pdf file hosted in an iframe. While this makes it easier to explain a service by not adhering to a website copy-type style of writing, the offering is much better defined than the previous two and is a great example to follow.
Strengths:
Structure is very strong, with distinct and rich sections for strategies, approaches, use cases, and focus in AWS.
The opening line, which says ‘Leverage a team of experts to successfully elevate your existing applications and unlock the power of cloud-native development’ gives us some key information. First, we’re employing a professional service delivered by (AWS) certified practitioners. Second, we know the service is related to cloud-native development. We highlighted earlier that modernization and cloud-native are not mutually inclusive. That still applies here, but at least the scene is set from the start.
The following paragraph describes the challenge very well, i.e. migration without modernization is unlikely to produce any benefit.
The strategies section provides an (almost) exhaustive list of techniques, including serverless refactoring, container adoption, and replatforming. Between the three, on-premises applications can be modernized to fit the purpose, rather than trying to refactor everything to microservices because it’s the cool thing to do.
The use cases section defines really well the target audience for the solution. Capitalizing on their specialization, enterprises with a legacy .NET application would unavoidably be attracted to Rackspace service as opposed to other competitors. SaaS-ifying applications is another use case that’s very specific, yet a very likely challenge among large enterprises.
The ‘our approach’ section describes the expected engagement in a good level of detail. Prospects will know what to expect and how to plan for an engagement with Rackspace.
Improvements:
While this offering ticks most of the boxes, the title misses an important aspect. Namely, the AWS specialty. The lack of alignment between the title and the AWS aspect of it begs the question of whether Rackspace can deliver the service for non-AWS clouds. To improve this, Rackspace can specifically call out AWS only or mention vendor-agnosticism.
Do Your Own Assessment for DXC
Now that we have evaluated the above offerings, check out DXC’s Application Modernization services and identify the good, bad, and ugly. You can ask questions such as:
- Would I understand the offering without prior knowledge of what the service does?
- How much substance is there on the page? Is there any website copy that does not provide information that is actually useful if I were to engage with the vendor
- Do I have visibility into how the engagement with the vendor works?
- Are there any identifiers that can help me understand whether the service is applicable to my specific problems?
- Do I know the output of the service?
Best Practices for Full Clarity
- Be generous on specifics – just as it’s good business practice to niche down, so is providing specifics for a service. The offering needs to include enough detail to educate customers on what the service is and how it’s delivered such that they have as few follow-up questions as possible. This not only helps prospects easily determine whether a service is suitable for their needs, but it also shortens the sales cycle and enables richer initial conversations. We have seen above why RackSpace’s offering was clearer and better defined than PWC’s or Cognizant’s.
- Collapse of the wave function – a concept borrowed from everyone’s favorite quantum physics phenomenon, an offering is open for interpretation unless it specifically mentions the inclusion or exclusion of a characteristic. For example, we saw Rackspace’s offering appears to be vendor agnostic, but they call out the AWS specialty in the ‘Why Rackspace’ section. Does that exclude other cloud providers? Whatever the answer, it should be clarified. If something is ambiguous, buyers are unlikely to give the benefit of the doubt.
Writing Sales and Marketing Collateral
An offering only exists when it is documented in a written artifact. Let’s explore some of those.
Sales Battlecards
A sales battlecard is a short, often one-page document that provides prospects a quick, easy-to-understand overview of an offering. It’s used by sales representatives to bring up in conversations with prospects to address objections and differentiators from competitors’ services. Battlecards are highly tailored to target specific industries, objections, and technical levels.
- High-level description – A battlecard can outline the specifics of the application development service, such as languages used, development methodologies (like Agile or DevOps), typical project timelines, and pricing structures.
- Differentiating features – These are capabilities that are less common in the market, which can include previous projects compliant with HIPAA or PCI, SOC2 accreditation, on-shore resources, and certifications from vendors such as AWS.
- Competitive Positioning – The battlecard can highlight how your application development service stands out from competitors. This could include factors like superior technical expertise, more flexible service offerings, better project management, or more effective communication.
- Handling Objections – Common objections in selling application development services might include concerns about cost, timelines, communication, or technical capabilities. A battlecard can equip sales reps with pre-prepared responses to these objections.
- Success Stories/Case Studies – Battlecards can include brief examples of past successful projects, which can be used to demonstrate competence and build trust with potential clients.
One-pagers
A one-pager is a succinct, single-page document that summarizes a product, service, or solution. Compared to sales battlecards, which are tools used by the sales teams during calls, one-pagers are designed for prospects to self-serve. It should highlight what the service is, key features and benefits of the service, and use cases. Visual elements like graphs or diagrams can add some visual interest and condense more information onto the page.
Solution Briefs
Solution briefs provide a chance to wrap a narrative around the service. These are longer documents that provide more detailed information about a specific service or solution, including its features, benefits, use cases, process, and technical and non-technical features.
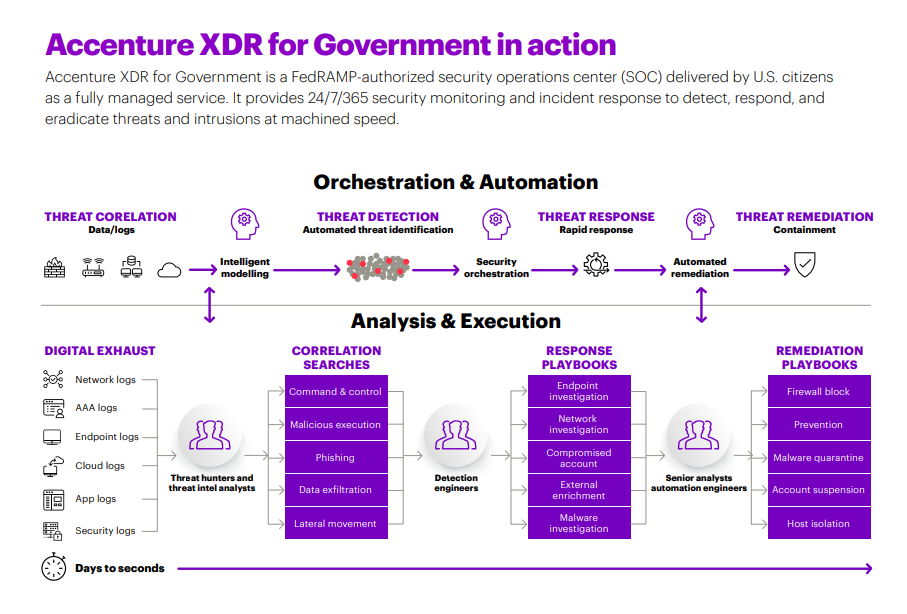
A notable example of a solution brief is Accenture’s Managed Security Service for the Federal Government. Here are some highlights from the solution brief:
- Hypothetical case
- Process diagram
- Industry-specific accreditations
- Quoted their own report, some statistics may not be known by the customer themselves
- Recognizes and plays off Zero trust
Blog Posts and Articles
Blog and articles are a fantastic opportunity to market services and built authority simultaneously. They serve multiple purposes, are publicly available and are search engine friendly. In the context of this book, we suggest using blog posts to tackle highly targeted challenges and use cases, which provide benefits such as search engine presence, reference documentation for customer engagements, and demonstrating subject matter expertise.
I came across Codilime multiple times for different topics while researching the networking space. While I’m no longer in a networks engineering role to purchase the service directly, I found the content they release so good that at the very least I can give them as an example for good technical blog posts.
These include goodies such as:
- Hardware offloading in software-defined networking
- How to avoid code duplication in Jenkinsfiles?
- Policy as code — what is it? Definition and tools
- Developing custom network functionality using SONiC
- From Kubernetes Ingress to Kubernetes Gateway API
- Handling L4/L7 traffic with Envoy proxy – Introducing Envoy
- Service mesh vs. Kubernetes Ingress – what is the difference?
- Network ACL processing algorithms—optimizing firewall’s performance
- Network traffic troubleshooting during VNF lifecycle – aspects of Tungsten Fabric flows
These are the types of hard problems only really researched when there’s a need for deep expertise.
Call-to-actions are highly important in this case. With the risk of spoiling an informative blog post with a sales CTA, prospects researching the space are a hot lead for the service.
Using ChatGPT or other LLMs
Don’t use LLMs to write content for you. Instead, Use them to surface ideas to speed up the content creation process.
Consider the following prompt structure:
|
Write a service offering for [type of service] service that uses [tools/technologies] to [what the service does] for [deliverable]. Provide details such as
|
Let us replace the variables with some examples:
|
Write a service offering for [an end-to-end data analytics and business intelligence] service that uses [Snowflake and Grafana] to [collect customer data from multiple platforms such as website and mobile application] to [produce real-time dashboards about usage and other metrics]. |
The LLM response highlights some important characteristics that, if relevant, can be used as reference points for defining the offering. Let’s see the challenges that the LLM produced:
|
LLM Pro tips
- If researching a topic or fact-checking an LLM response is difficult, exhausting, time-consuming, or not possible in a given time frame, use another LLM, such as https://open-assistant.io/ with the same prompt. It is unlikely that two LLMs with different underlying models(!) hallucinate in the same way. Using two or more LLMs can produce one of the following scenarios. First, the responses from the LLMs align, which means there’s a higher likelihood for the responses to not be wrong or not be hallucinated (notice I did not say correct). Second, the LLM responses disagree, which means that either one, or both are fabricated, and require the user to fall back to researching reputable resources.
- Be aware of leading or loaded questions when submitting prompts. A prompt such as ‘why is X better than Y’ is less likely to produce an accurate response. A lot of advice for writing prompts suggests that the input needs to be as specific as possible, but almost all biases can infiltrate a prompt and skew answers. ‘Describe ingress controllers in the context of container networking, and then list and describe open source, ingress controllers’.
- LLMs can actually surface excellent ideas, albeit the accompanying descriptions are mediocre and repetitive. If the content produced by the LLM seems generic and uninteresting, it is likely the prompt needs to be better defined. Flat LLM responses are a great sanity check to validate whether the offering described in the prompt is interesting.
Common Marketing Copywriting Pitfalls
I’ve condensed this non-exhaustive category into three categories. Namely, sweet nothings, infomercials, and internal jargon.
Sweet Nothings
Typically referred to as marketing speak, are phrases which try presenting benefits without context or backing. These are not inherently bad, but often need more to them than just a couple of words. For each of the examples below, I will also describe how to rewrite them such that they can fulfill their intended purpose (and also do better SEO-wise).
- “Simplify operations” – can be improved as follows: “simplify operations by aggregating all your network data onto one platform”
- “Reduce risks” – you’d be better of saying: “automate the discovery of security vulnerabilities to reduce risks”
- “Increase customer satisfaction” – a better version would be: “increase customer satisfaction by ensuring 99% uptime and <20ms latencies”
Sweet nothings can also be longer than just ~3 word headings. For example, can you tell me, just from this paragraph, what the solution is?
“To bring IoT to life, your business requires close synergy between business needs and the technology stack needed to connect and manage billions of devices simultaneously”.
Infomercials
This “has this ever happened to you?” type of copy intends to make the readers problem-aware. However, I would argue that we should write landing pages with the assumption that the IT buyers are already aware of the challenges they face. I don’t browse enterprise IT websites for fun to end up on a landing page and think: “you know, I am actually drowning in IT tickets”.
- “Never […] again” – Never miss responding to a support ticket again!
- “Stop […]” – Stop manually approving your employee’s holiday requests!
I don’t have any recommendations to improve those. I would just strongly advise you to take them out.
Internal Jargon
This one assumes that readers who are not aware of your company or product would understand what you mean without explaining it first. This leads to readers thinking “You keep saying this, but I don’t know what you mean”. Terms such as Application-led Migration, Hybrid Connected EdgeOps and the like.
- Landing page: We are a leading NGDDoSPaaS provider.
- IT Buyer: What’s NGDDoSPaaS?
- Landing page: It’s Next Generation Distributed Denial of Service Protection as-a-Service.
- IT buyer: Okay, how does Next Generation DDoS Protection work and how’s it different to a DDoS protection service?
- Landing page: Download our whitepaper to see how we reduced DDoS attacks by 300%!
- Whitepaper: “In a post-COVID world, cybersecurity is of paramount importance.”
Decency is Not a Differentiator
A lot of professional IT firms try to leverage values such as honesty, integrity, and passion as reasons for prospects to select them over competitors. These are not and should not be used as differentiators for two reasons. Firstly, writing some website copy for how the company has a people-first approach does not translate into how the company actually behaves. Second, these types of values need to constitute the basis of every human interaction. Just as ‘our workforce uses desktops and laptops to do their jobs’ is a redundant statement, so is ‘we have a strong moral compass’.
Would Your Offering Win a $100m Contract?
Let there be a Request for Qualification/Proposal (RFP/RFQ) for a $100m contract for a digital transformation project for a multinational organization. This exercise evaluates not your core technical capability for delivering the service, but rather the ability to scale and deliver on a large project. Now, let’s go through the following process:
- Determine what the expectations for a contract this size are.
- Realistically select what capabilities are available, or can be procured in case of winning (such as hiring more people).
- Use the available capabilities to create the most scalable and secure version of your offerings.
- Scale down to create more accessible versions of the service.
How Would a $100m Deal Look Like?
Working with an enterprise and organization with multinational presence to define a long term (>5 year) contract that includes design, build, and run activities.
- Project and delivery management – deliver multiple simultaneous projects, knowledge across multiple verticals The ability to work with cross-discipline teams, including business, operations, finance, and other technical teams is crucial. The provider should demonstrate expertise in project management and stakeholder management.
- Global Scalability – The provider should have proven experience in scaling services internationally. They must be able to manage multiple legal entities, abide by various regional regulations, and work in different timezones.
- Data Management – demonstrate robust capabilities in data management, including data governance, data integration, data analytics, and business intelligence. They should be able to help the client leverage their data to drive business decisions.
- Secure by design – incorporating cybersecurity principles into every stage of development for new products or services. It emphasizes creating solutions that are resilient against threats by considering security risks early on, instead of retrofitting protection measures later
- IT Service Management (ITSM) –The provider should follow ITSM best practices for delivering IT services, focusing on the quality of the services and customer satisfaction. They should also be well-versed in ITSM frameworks like ITIL.
- Hybrid IT Management – The provider should be adept at managing hybrid IT stacks – a mix of on-premises, private cloud, and third-party, public cloud services with orchestration between the platforms.
- Security and Compliance – this includes having on-shore resources, following security best practices, and holding certifications such as SOC2, ISO 27001, and Cyber Essentials+. The provider should also be able to demonstrate their capacity to comply with data privacy regulations like GDPR, CCPA, etc.
- Governance and Reporting – demonstrat strong governance structures and reporting capabilities to provide regular, transparent reports on project progress, performance metrics, and other key data. They should also be able to adapt their reporting to the specific needs and formats of the client organization.
- Tenure, Stability and management – A contract of this magnitude requires a provider with solid financial stability. The client will likely conduct a financial audit to ensure the provider is in good standing and can handle the financial demands of the contract.
Walking the Walk With Precism
For this book’s call-to-action, we shall employ the tools presented in this book to create our professional service offering, technical content writing.
Technical Content Writing for Enterprise IT
We help businesses in the B2B technology space to improve their public-facing resources, downloadable assets and internal documentation. We aim to offer your prospects all the necessary information to educate themselves on your technologies when conducting product research and market analysis.
To produce clear and convincing marketing and sales technical content, enterprises need to leverage skills from different areas in the business, which include technical knowledge, copywriting, and industry awareness. While coordinating all these efforts leads to long turnaround times and high costs, producing content without all three components leads to either technically inaccurate content, hard-to-understand assets, or poor positioning in the market.
Precism sits at the overlap between all three key skills, providing you with a single point of contact for producing written assets such as articles and blog posts, ebooks and whitepapers, datasheets, solution briefs, and website copy. Our writers have experience from both the buy and sell sides of IT services, with areas of expertise including networking, security, cloud, edge, data infrastructure and analytics,
To produce content that best highlights your competitive differentiators, Precism produces content with the following process:
- Understanding your offerings – we learn about your services and offerings by reading technical documentation, available collateral, and interviewing stakeholders.
- Scope definition – we align your brand and content strategy to highlight your unique differentiators. Agreeing on the types and volumes of collateral to be produced
- Service Delivery – we engage with your internal marketing, technical, and business stakeholders to produce content that’s technically relevant, in line with your brand, and demanded by the market.
- Feedback Cycles – Two formal reviews included with every piece of content produced, each cycle with a less than one week turnaround time
- Engagement monitoring and iteration – Working with your product, sales, and marketing teams to gauge the level of engagement and identify improvement and optimization opportunities.
About the Authors
Iris Green
Iris brings together her background in Communications and Public Relations with her technical expertise in cybersecurity to help enterprises clearly define and articulate complex value propositions. After having helped dozens B2B technology companies refine their messaging, Iris decided to formalize these efforts and co-founded Precism.
Andrew Green
Andrew is a technology research analyst and writer with a background in engineering and product management. He has a deep understanding of how enterprises work in terms of governance, supply chain management, compliance, and stakeholder management, which he uses to help businesses streamline the selling and onboarding of new services.
Annexes
Cognizant Application Modernization
|
Drive digital CX and business outcomes We engineer applications for modern businesses. We help organizations deliver maximum digital value and unleash an unbeatable competitive advantage by leveraging modern software engineering principles, homegrown platforms, deep industry expertise and strategic partnership networks.
Accelerate digital with predictable outcomes Modernize applications, improve technical value, harness cloud-based development and develop your digital portfolio with our Cognizant® Modernization Acceleration Platform, Cognizant Cloud Acceleration Platform and extended third-party tools.
Application-led cloud migration Employ a platform-driven approach to cloud migration, making applications digital-ready while ensuring business agility and elastic scalability. Legacy modernization Modernize legacy applications and their ecosystem to a cost-effective modern platform, using a fully automated, tools-based approach. Technology stack modernization Upgrade technology cost effectively, and migrate applications with automated assessments and remediation. Business-led modernization Unlock the future value for the business and improve speed to market using our Digital Footprint Diagnostics.
Cognizant Modernization Acceleration Platform Industrialized, insights-driven approach for strategizing modernization Cognizant Modernization Acceleration Platform is a unified and comprehensive platform that defines and orchestrates your modernization strategy and execution by leveraging proprietary IPs and partner tools across the modernization lifecycle. Our platform enables automated discovery, portfolio analysis and execution planning to derive the modernization strategy and further enables contextual solution recommendations by using Modernization Acceleration Kits for faster execution. |
PWC Application Modernization Offering
|
Application and data modernization solutions Move beyond migration to embrace modernization. Companies are looking for ways to rethink their business models and processes to drive more collaboration, respond more rapidly to fluctuating market changes and improve overall user experiences. With modernization, businesses can create even more value and accelerate their transformation through reinvention:
Reinvent what’s possible: Our application modernization solutions help your business rebuild and redesign new cloud architecture and operating systems designed to increase agility, flexibility and scalability across critical business functions. As a result, your business moves from an outdated legacy system to a modern infrastructure with on-demand resources.
Our approach to modernization We’re reinventing the way your applications and infrastructure are built using our industry expertise and leading cloud-native tools and technologies. With our iterative build approach, we help your business become more efficient and responsive to quick changes. We leverage our industry standard automation tools and cloud service providers (CSP) funding models to build a cloud modernization strategy that aligns with your business. Here are some of the modernization approaches we have experience in:
Monolith to Microservices Microservices are a collection of smaller, independently running bits of code that make complex cloud applications faster and easier to scale. We can help you break up large monolithic applications into singular units for scalability and increased agility.
Containers and Kubernetes Containers contain essential software components to run in a self-sufficient, isolated environment; they make your applications in the cloud work more efficiently. We have extensive experience working with open source platforms such as kubernetes to simplify the management of your containerized workloads.
Serverless architecture Serverless architecture is a way to build applications without requiring server management. Serverless allows developers to focus on your application development instead of the headaches of managing and operating servers or runtimes.
Mainframe modernization Mainframe modernization improves legacy mainframe infrastructure and applications. Our end-to-end solutions reinvent costly, traditional mainframes by bringing them to the cloud to ensure business agility and operational excellence.
Migration Migration moves your most critical applications and data centers securely to the cloud. With a business-led approach, we go beyond the technical elements of lifting and shifting your workloads to focus on your end goals. |
Rackspace’s Application Modernization Offering
|
Application Modernization Leverage a team of experts to successfully elevate your existing applications and unlock the power of cloud native development.
Early approaches to cloud adoption focused on infrastructure and application migration, with very little attention to the underlying code. While the cloud delivered the benefits of elasticity and scale, its full benefit can’t be unleashed without application modernization.
Cloud native application development allows you to unlock the full potential of running applications in the cloud. If you’re hindered by the complexity of public cloud technologies and modern architectures, we’re here to help with guidance and support for reengineering your applications and updating your workflows. With specialization in .NET to .NET Core, cloud native SaaS platforms and a proven framework for monolith to microservices decomposition, we’re ready to help you maximize the agility, reliability and cost-saving benefits only the cloud can deliver.
Modernization Strategies There is no one-size fits all pathway to modernization. Our architects will assess your applications and infrastructure in the context of your business goals and your team’s strengths to determine which combination of cloud technologies and architectural patterns will best fit your long-term roadmap: Serverless refactoring: Build self-healing, auto-scaling, applications, unchained from the limitations of servers. Serverless architectures offer the highest efficiency and cost benefits of the cloud by pushing nearly all infrastructure and software management to the platform. Container adoption: When serverless isn’t an option, containers are the preference for deploying modern, complex, distributed applications. Containers often require minimal changes to the application, making them the perfect evolutionary step when significant refactoring isn’t appropriate Cloud-Native Replatforming: Incrementally modernize your application by adopting managed platform services as drop-in replacements for databases, messaging, API management, logging, monitoring, alerting and more.
Use Cases NET to .NET Core: Eliminate pricey Windows licenses by leveraging containers and serverless technologies in your legacy applications. After performing a thorough audit of your codebase and application architecture, we’ll recommend and execute on a strategy to refactor your legacy
.NET applications to .NET Core. Monolith to microservices: A key tenant of a modern application is organizing it into logical services that can be developed, scaled and deployed independently while giving service teams the freedom to choose the appropriate technologies for their needs. Our experts can accelerate your effort to break up your existing monoliths by applying proven techniques to incrementally refactor your application without requiring years of investment or stopping new feature development.
SaaS-ify legacy apps: Users are demanding an application experience that is available anytime, anywhere and constantly updated without the need to manage and run software. By refactoring your legacy desktop, on-premises and singletenant applications to be delivered in a web and mobile SaaS model, you can reach these users while improving your product and reducing your operating costs and complexity. We can guide and accelerate your SaaS journey with our unique experience in building and refactoring SaaS application in the cloud
Our approach Assessment Through a collaborative process, our team of business analysts and architects will review your application portfolio to understand existing architectural patterns, infrastructure, tools, and processes. We’ll evaluate the current state against business, functional, technical, and cost objectives and align your teams’ skills and gaps with modern development processes and technologies.
Roadmap and Design Based on the assessment and your business goals, our solution architects will categorize your applications by modernization approach and design a reference, blueprint architecture. We’ll select tools and technology and define a roadmap that focuses on early wins that build momentum and maximize ROI.
Pilot Project Following the adage of “think big, start small”, we’ll start the modernization with a pilot project that focuses on defining repeatable patterns, rapid delivery and demonstrating business value. Through hands-on work, our teams will continue to refine the architecture and processes that enables large scale modernization of your portfolio.
Large Scale Modernization Building on the momentum from the pilot project, our team will consolidate best practices into a foundational platform that enables building, deploying, and operating modern applications at scale. Our delivery process prioritizes agility and transparency, enabling your teams through our “do with” development approach |
DXC Application Modernization
|
Applications Modernization Drive digital CX and business outcomes Unlock value through apps modernization Drive out costs and simplify
Capabilities Mainframe modernization EXPLORE MORE |
Accenture’s Managed Security Services for Federal Gov
|
Securing the Government Enterprise The Case for Managed Security Services Federal government agencies face unique and growing challenges in securing their enterprise from cyberattacks. They have a higher threat profile than many of their commercial counterparts, coupled with institutional constraints in acquiring, hiring, and implementing the critical resources needed to fully protect their agency. Against these challenges, managed security services like extended detection and response (XDR) can dramatically improve their overall cyber resilience, enabling them to detect, defeat, and recover from increasingly sophisticated attacks faster and more confidently. By standardizing and automating core security operations and integrating streaming analytics and threat intelligence, XDR can improve overall performance, financial predictability, and cost-effectiveness. While federal agencies perform admirably in protecting their environments, many are asking if their current cybersecurity cost structure is sustainable, especially as attacks become pervasive. According to Accenture’s Third Annual State of Cyber Resilience Report—Federal Edition, most (75 percent) federal agencies report year-over-year cost increases for cybersecurity, with 1 in 5 reporting cost increases exceeding 25 percent. Leading this charge were higher costs for network security, threat detection, and security monitoring. As a result, 60 percent of these federal leaders say these cost increases are unsustainable. Federal agencies face a host of inherent constraints that make protecting their networks and infrastructure both costly and challenging. These factors include an inability to readily hire qualified talent, an overly complicated IT architecture and environment that is expensive and difficult to protect, pervasive compliance mandates, and a procurement system not conducive to agility. These factors leave too many federal agencies reliant on highly manual processes, outdated technologies, and understaffed and undertrained security operations centers (SOC) to protect their exceedingly fragmented environment against a growing number of more sophisticated attacks. Zero trust takes center stage
|
Contact us
Let’s walk through your technical sales and marketing collateral requirements.